The cryptocurrency world while filled with technological innovation and opportunities for financial gain, also present significant risks and scams. One of the most used techniques is phishing attacks. These simple yet effective scams have led to a steady rise in financial losses within the crypto community. What is a phishing attack? And how can they be avoided? Find out more in the following article.
Article Summary
- 🦹♂️ Phishing is a scam that “fish” or bait victims to provide sensitive data such as passwords or private keys.
- 📨 Email and social media platforms such as X, Discord, and Telegram are hotbeds for scammers to spread their phishing links. Methods include sharing airdrop links, impersonating official accounts, and pretending to be the support team.
- 💣 Recorded losses caused by phishing attacks during January-September 2024 have reached $468 million.
- 🔎 The best way to avoid phishing attacks is always to be vigilant, verify, and not just click on website or email links.
What is a Phishing Attack?
Phishing is a scam that “fish” or bait victims to provide sensitive data such as passwords or private keys. This type of scam is one of the most popular and common scams. These scammers use various mediums such as social media, private messages, and email. In addition, this is also one of the ways hackers steal Bitcoin from digital wallets.
Phishing scams usually come in the form of messages on behalf of an important organization or person. This message then invites the victim to follow instructions, such as entering the link sent or sending tokens to a specific address.
Perpetrators will hide ransomware or spyware behind these links to obtain important information from users. In a more advanced crypto phishing, the victim will immediately lose his crypto assets when using the link provided by the fraudster.
In addtion to phising attack, the following are some of the scams that are rampant in crypto.
Phishing Attack Methods
“X (formerly Twitter) has been a primary platform for hackers to execute phishing attacks. Given its widespread use among crypto communities and as a channel for official project accounts, X users have become prime targets for hackers.
Scam Sniffer reports that a common phishing tactic is impersonating other X users, including celebrities and official project accounts. Victims are typically lured to phishing websites through tweets containing links from these imposter accounts.

A recent trend in phishing attacks is permit phishing, where victims are tricked or coerced into approving a seemingly harmless transaction. However, this approval allows hackers to steal the victim’s tokens. Once they gain control, hackers drain the victim’s wallet.
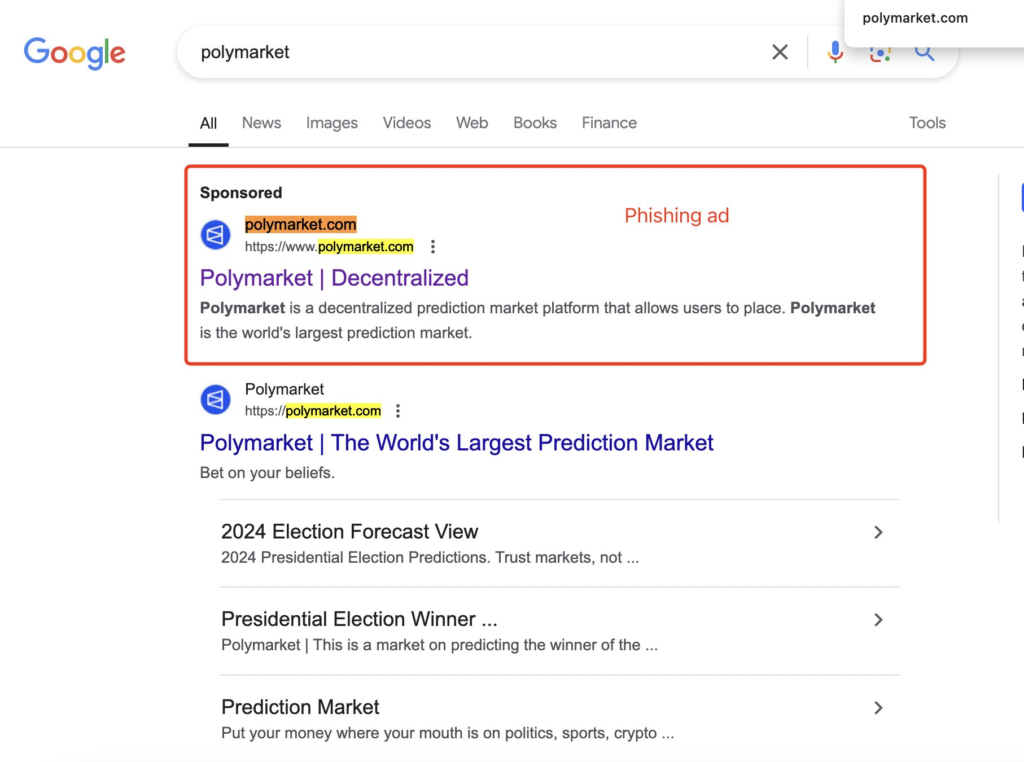
Besides X, phishing links are often disseminated through Google ads and impersonating project support teams on platforms like Discord or Telegram. These imposters offer assistance while sending phishing links.
Ethereum blockchain is the primary target for phishing attacks due to its high liquidity and widely known smart contracts. Hackers exploit open-source contracts to create phishing links or develop realistic smart contracts to deceive unsuspecting victims.
The DeFi sector has become a common hunting ground for scammers. Learn how to use DeFi safely here.
Phishing Attack Cases in the Crypto Industry
According to CoinTelegraph, cryptocurrency phishing attacks resulted in losses of $127 million in the third quarter of 2024 alone, with approximately 11,000 victims falling prey each month.
Before this, Scam Sniffer reported total losses of $314 million due to phishing attacks in the first half of 2024. This represents a significant increase compared to the $295 million lost to phishing in 2023.

In total, $468 million was stolen through phishing attacks between January and September 2024, with $46 million occurring in September alone.
Scam Sniffer’s report indicates that there were 10,800 phishing victims in September. The largest loss occurred on September 28th when a permit phishing signature attack drained 12,083 spWETH valued at $32.43 million.
How to Identifying Phishing Attack
Identifying phishing attacks can be challenging as scammers go to great lengths to create convincing emails and websites. However, there are several red flags to watch out for:
- Misleading links. Phishing links often redirect victims to fake websites that mimic legitimate ones. These links are usually shortened or slightly modified from the original version to deceive potential victims. For example, if Jupiter distributes an airdrop through www.aidropjupiter.com, a phishing attack might use a shortened link like bit.ly/airdropjupiter or a modified version like www.airdropjup.com. Scammers sometimes substitute the lowercase letter ‘i’ with a lowercase ‘l'(L).
- Spelling and grammatical errors. Phishing emails often contain mistakes in spelling or grammar. Phishers are usually in a hurry to get their message out and don’t take time to proofread. The language used may not be the scammer’s native tongue, resulting in numerous mistakes. A high number of spelling or grammatical errors strongly indicates a phishing attempt.
- Using public email instead of a corporate one. Attackers often use a public email account because it is easier to create a fake email with a public domain than a corporate one. Hence, an official-sounding email that ends in “@gmail.com” instead of “@companyname.com” should immediately arouse suspicion.
- Content Misalignment. It’s difficult to replicate a website perfectly; scammers often miss small details. Inconsistencies in language style, design, or calls to action can be telltale signs of a phishing attempt. For example, an email might instruct you to “click here to log in,” but the button says “click here to sign up.”
How to Avoid Phishing Attack
Phishing attacks have proven to be a simple yet highly effective method. The modus operandi remains consistent: preying on the unwary victims. The best defense against phishing attacks is vigilance and caution. Here are some tips to help you stay safe:
- 👀 Always be cautious of emails with attachments or links. If you’re unsure about an email, ignore it or contact the sender to verify its authenticity.
- 🔍 Always verify the authenticity of social media accounts that share links. Avoid clicking links or downloading attachments without verifying the account’s legitimacy.
- 🚨 Be wary of websites that look suspicious or too good to be true*.* If in doubt, use a web search to see if there are reports that the website is fake.
- 💡 Use third-party extensions that can increase security. However, make sure the third party is credible and has a track record that can be trusted and accounted for.
- 🔑 Enable two-factor authentication and avoid using the same password for multiple accounts.
- ⛔ Do not share personal information, such as private keys, with anyone.
- ⚠️ Use a VPN when connecting to the internet, especially if using public Wi-Fi.
Scams are also common in the NFT world. Learn the types of scams to avoid becoming a victim.
Conclusion
Phishing is a scam that “fish” or bait victims to provide sensitive data such as passwords or private keys. Recently, a new tactic known as permit phishing has emerged, where victims are tricked into approving seemingly harmless transactions. Unbeknownst to them, this approval allows hackers to drain their entire wallets.
The key to avoiding phishing attacks is to remain vigilant, verify information, and avoid clicking on suspicious links or emails. Additionally, using third-party applications to check the security of links and websites can provide an extra layer of protection.
Buy Crypto Assets on Pintu
Looking to invest in crypto assets? No worries, you can safely and conveniently purchase a wide range of cryptocurrencies such as BTC, ETH, SOL, and others safely and easily at Pintu. Pintu diligently evaluates all its crypto assets, highlighting the significance of being cautious.
Pintu is also compatible with popular wallets such as Metamask to facilitate your transactions. Download Pintu app on Play Store and App Store! Your security is guaranteed because Pintu is regulated and supervised by Bappebti and Kominfo.
Aside from buying and trading crypto assets, you can expand your knowledge about cryptocurrencies through various Pintu Academy articles. Updated weekly, all Pintu Academy articles are made for knowledge and educational purposes, not as financial advice.
References
- Guneet Kaur, What is a phishing attack in crypto, and how to prevent it? Coin Telegraph, accessed on 22 October 2024.
- Erick Huffman, What is a Phishing Attack? Technopedia, accessed on 22 October 2024.
- Chainanalysis, Targeted Approval Phishing Scams See Explosive Growth Over Last Two Years, With At Least $374 Million Suspected Stolen in 2023, accessed on 22 October 2024.
- Arijit Sarkar, Crypto phishing scams drained $46M in September, Coin Telegraph, accessed on 22 October 2024.
