The crypto industry is known for its ongoing evolution. Every blockchain projects compete to present the latest technological breakthroughs. Unfortunately, the development of the crypto ecosystem has not been immune to the attacks of irresponsible parties. Crypto attacks continue to occur yearly, and the numbers continue to increase.
As investors, we certainly don’t want to be victims of crypto attacks. Therefore, knowing the various types and how they operate can help us lower the risk of crypto attacks. Read the explanation in the article that follows.
Article Summary
- 👊 Crypto attack is an attack that attempts to exploit blockchain networks, wallets, or crypto asset transactions.
- 🚨 In 2022, crypto attacks have caused losses of up to US$ 3.8 billion, marking a 15% increase from the previous year.
- 🔎 Some crypto attacks that often occur are flash loan attacks, phishing attacks, cryptojacking, dusting attacks, and 51% attacks.
- 🔒 Staying vigilant, updating your software, using additional security tools, and continuing to learn new trends in fraud can be the most effective way to avoid crypto attacks.
What is Crypto Attack?
A crypto attack is an attack that attempts to exploit a blockchain network, wallets, or crypto asset transactions. The main goal of a crypto attack is to take advantage of the victims. In crypto attacks, the victims can be retail investors or crypto industry players such as exchanges, decentralized finance (DeFi) applications, and blockchain networks.
Although the crypto industry and ecosystem continue to grow, crypto attacks are still rampant. Based on a report from Chainalysis, 2022 recorded the worst crypto attack loss value of all time. It was recorded that US$ 3.8 billion was stolen from the crypto industry. This figure has increased by 15% from the previous year.
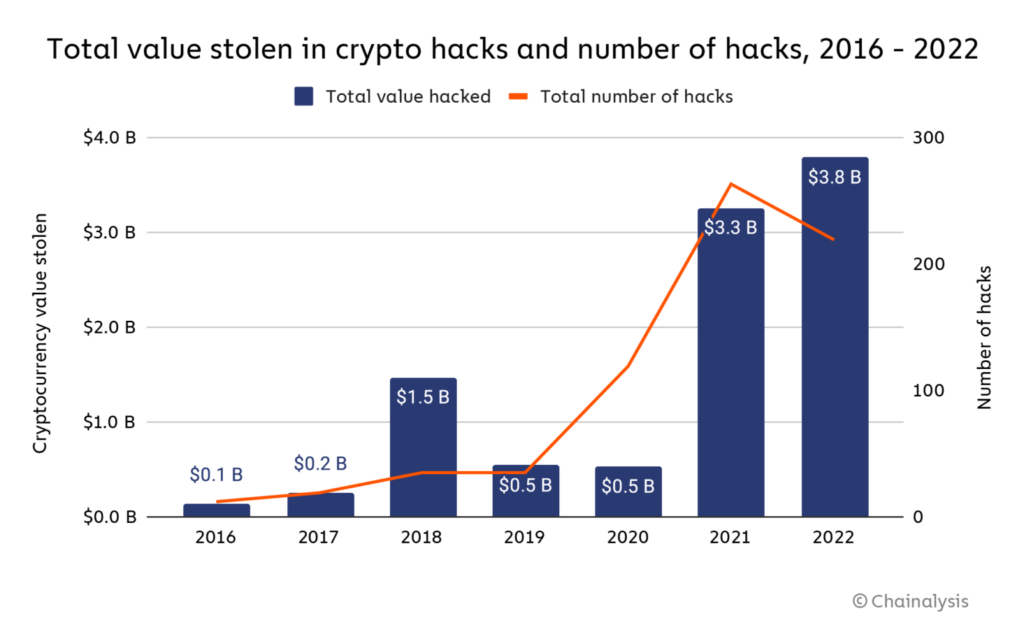
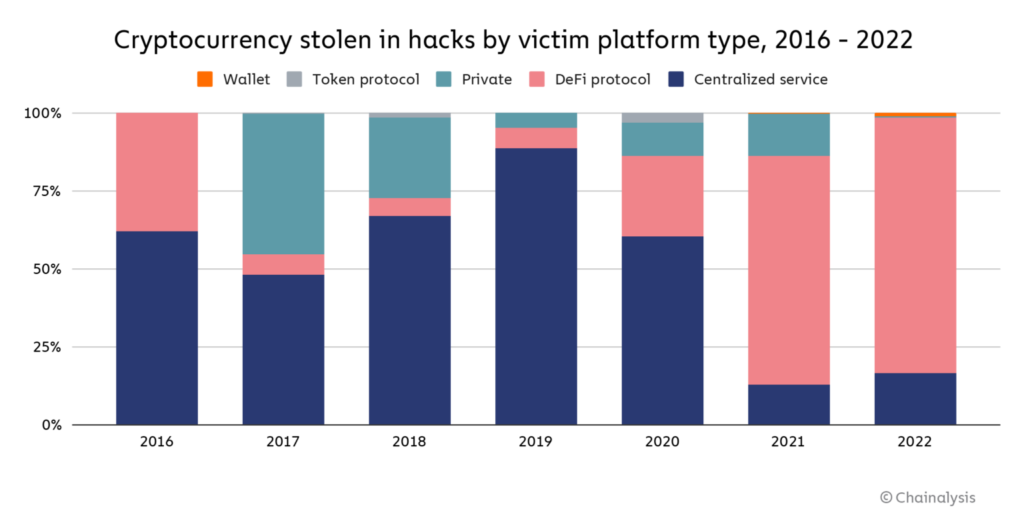
The DeFi protocol is the primary victim of crypto attacks. As much as 82.1% of all crypto attacks occurred on the DeFi platform. This means that US$ 3.1 billion has been stolen from the DeFi protocol throughout 2022, up 73.3% from 2021.
How Does Crypto Attack Works
In carrying out their actions, hackers can attack in two ways: active and passive. In an active attack, the hacker will attempt to access the victim’s sensitive data at all costs. After gaining access, the hacker will damage and tamper with the data.
While in a passive attack, the hacker only attacks to gain access to the victim’s sensitive data, such as private keys by intercepting the data. However, the hacker will not damage or tamper with those data.
Types of Crypto Attacks
The following are five types of crypto attacks that commonly happens in the crypto industry:
1. Flash Loan Attack
Flash loan attack is one of the attack methods that occur on the DeFi platform. Users can borrow monet using the flash loan service without providing collateral. A smart contract that enforces the flash loan method ensures that all requirements must be met before the loan can be approved.
Unfortunately, if hackers understand how the smart contract works, flash loan services become vulnerable to attacks. Flash loan attackers will find ways to manipulate the market while fulfilling smart contract rules. For this to work, the process must happen fast, and the debt must be repaid to the protocol in time. Otherwise, the transaction will reverse.
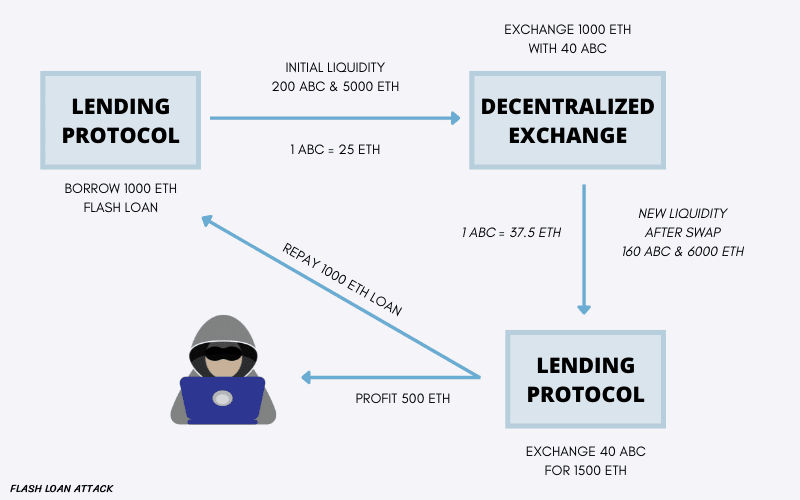
The most commonly used market manipulation method is arbitrage. The attacker will exploit the different asset prices on the two exchange platforms. Flash loan attacks can result in significant financial losses for the affected DeFi platform and its users.
An example of a flash loan attack occurred at PancakeBunny, a BSC-powered yield farming aggregator protocol. At that time, the attackers borrowed a large amount of BNB from PancakeSwap. Then, the BNB was used to manipulate the prices of USDT/BNB and BUNNY/BNB in the Pancake Bunny liquidity pool. The hacker then managed to get a large number of BUNNY tokens which they dumped on the market. Then, the hacker paid his debt on PancakeSwap so that his smart contract would not cancel the transaction. Through his actions, the hacker made a profit of up to US$3 million while the BUNNY token crashed.
You can learn more about how smart contracts work in the following article.
2. Cryptojacking
Cryptojacking is an attack where attackers infect a victim’s device with malware that mine cryptocurrency without the owner’s knowledge. Then, the successfully mined crypto will go directly to the hacker’s wallet. With this method, hackers will get the crypto without having to spend a penny. However, cryptojacking can only be done on crypto assets with proof-of-work (PoW) consensus.
In the case of cryptojacking, victims are less likely to realize that their device has been cryptojacked. This is because cryptojacking does not involve the theft or corruption of any personal data. But, the victim will pay the electricity bill without receiving the mining results (even if their computer successfully guesses the target hash).
Hackers can perform cryptojacking by creating a few lines of JavaScript code or a command line embedded in the HTML code that automatically runs the program when opened. Generally, hackers will use phishing methods to get victims to open certain web pages.
One of the most well-known cases of cryptojacking occurred in 2017. A JavaScript cryptojacking software was discovered on the Pirate Bay website mining Monero on users' computers. This was revealed after users reported an increase in their CPU usage rate after accessing the Torrent website. The Pirate Bay was able to mine a lot of Monero through cryptohijacking up until the issue was fixed.
3. Phishing Attack
Phishing is a scam that “fish” or baits victims to provide sensitive data such as passwords or private keys. This type of scam is one of the most popular and common scams. These scammers use various mediums, such as social media, private messages, and email. In addition, this is also one of the ways hackers steal Bitcoin from digital wallets.
Phishing scams usually come in messages on behalf of an important organization or person. This message then invites the victim to follow instructions, such as entering the link sent or sending tokens to a specific address.
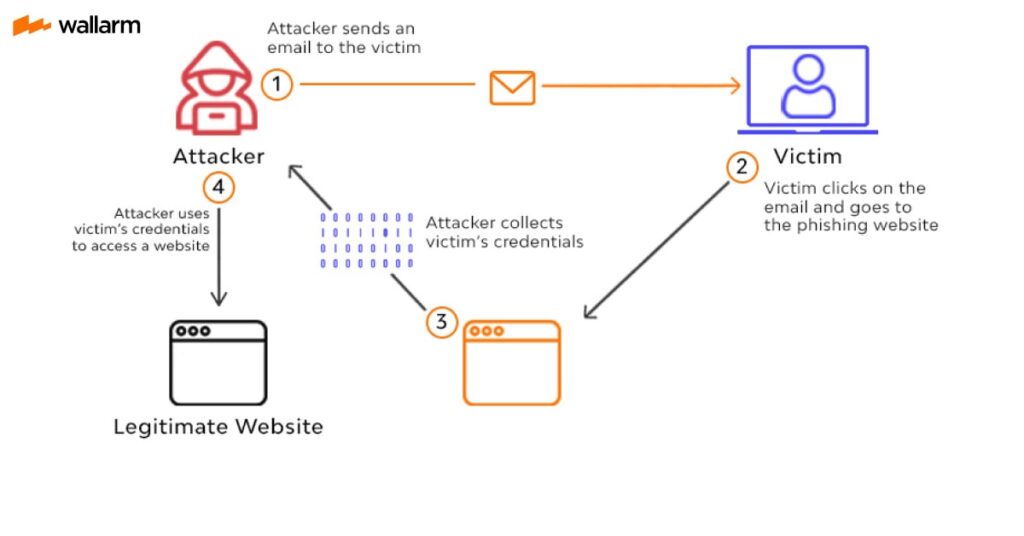
Behind the link, the perpetrator will hide ransomware or spyware to obtain important information, such as crypto wallet data. In more advanced crypto phishing, the victim will immediately lose his crypto assets when using the link provided by the fraudster.
The attack on Axie Infinity’s Ronin Bridge is one of the crypto fraud incidents that have happened as a result of phishing. According to the Block, the scammers offered a fictitious high-paying job to one of the senior developers of Axie Infinity. The employee downloaded a pdf file from the scammers. After that, the hacker was able to access several validator nodes of Axie Infinity and managed to steal around $540 million US dollars.
Phishing is also the most popular method of scamming, find out about other methods in the following article.
4. Dusting Attack
A dusting attack is a type of attack where an attacker sends small amounts of the cryptocurrency (known as “dust”) to a large number of addresses. Attackers do dusting attacks in order to de-anonymize the owners of those addresses. Dusting attacks can be challenging to detect because they resemble Unspent Transaction Output (UTXO) or a leftover crypto asset from an executed transaction.
If the crypto assets sent through the dusting attack were used for transactions, the attacker could see a list of transactions and their destination addresses. Later, the attacker can use this information for various purposes, such as phishing, scams, or targeted spam campaigns.
However, dusting attacks are not always dangerous. The reason is that blockchain analysis institutions deliberately carry out dusting attacks to conduct research or have cooperation contracts with the government. Dusting attacks can also be made to test the throughput or bandwidth of a network.
A dusting attack happened to Litecoin in 2019. At that time, someone discovered hundreds of thousands of dust transactions on the Litecoin network. After being traced, the source of the dusting attack came from a group advertising Litecoin mining. Fortunately, this attack harmed no one because it was only limited to spamming.
5. 51% Attack
51% attack is an attack on a cryptocurrency blockchain by a group of miners who control more than 50% of the network’s mining hash rate. By owning a dominant level of control, the group can do double spending, prevent transaction confirmation, and reverse the confirmed transactions.
However, 51% of attacks require a lot of capital because hackers need to have a lot of computing power to control 51% of the total hash power. Attackers are also in a race against time as they must constantly verify new transactions and create new blocks to outwit other miners.
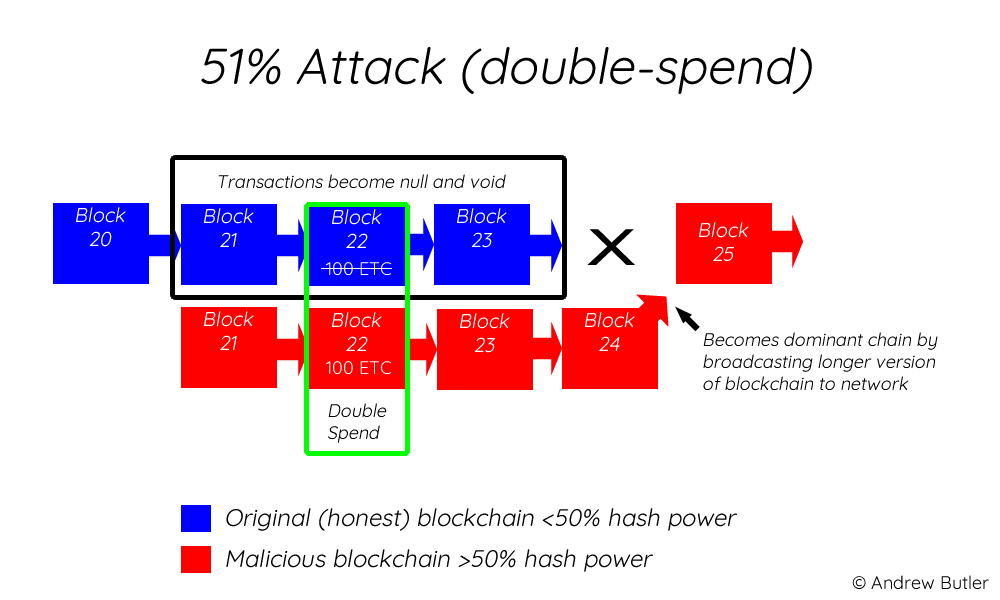
Thus, a 51% attack require a lot of electricity. Especially if the blockchain is a large network and has a good level of decentralization. Therefore, in some cases, 51% attacks occur on relatively small blockchain networks.
A 51% attack occurred on the Bitcoin Gold network in 2018. Given Bitcoin Gold's relatively low hash rate, the attackers dominated the network and did double-spending. Reportedly, the perpetrators of this 51% attack managed to reap profits of up to US$ 18 million.
Want to know more about how a 51% attack works on a blockchain? Read more here.
How to Prevent Crypto Attack
The following are some tips that you can apply to prevent and minimize being exposed to crypto attacks.
- Using Cold Wallet. Given that crypto attacks occur in the online world, storing your crypto assets data, such as wallet addresses and private keys offline, can be an option. This cold wallet method is done by storing data in a hardware or paper wallet.
- Keep Your Private Keys. The most important crypto security principle is that no one else should know your private key. If they do, they can access all your assets. Most phishing cases aim to gain access to your private key.
- Using Additional Security Apps. Using two-factor authentication (2FA) can provide additional security. The 2FA feature is handy when your password has been stolen. Fraudsters can’t access your account without authentication from a 2FA app like Google Authenticator.
- Ensure Software is Up-to-Date. Every software update comes with the latest updated level of security. This can reduce the risk of the software being exposed to malware attacks and other potential vulnerabilities.
- Always be vigilant. The essential ammunition to avoid crypto attacks is always vigilant. You must also deepen your knowledge by knowing the latest trends related to the crypto industry’s potential and mode of crime. Don’t be carelessly tempted by fraudulent threats from e-mail, social media, and websites.
Keep in mind that there are many other types of crypto attacks. The security landscape in the crypto industry is also ever-changing, given the industry's dynamic nature. Therefore, investors must deepen their knowledge, be vigilant, and apply risk mitigation when investing in crypto assets.
Self-custody is one way to store crypto safely. Learn how in the following article.
Buying Cryptocurrencies in Pintu
Pintu gives you a safe and easy platform to invest. You can invest in various crypto assets such as BTC, ETH, SOL, and others safely and easily.
Pintu is also compatible with popular wallets such as Metamask to facilitate your transactions. Download Pintu app on Play Store and App Store! Your security is guaranteed because Pintu is regulated and supervised by Bappebti and Kominfo.
In addition to executing transactions, in the Pintu Apps, you can also learn more about crypto through various Pintu Academy articles which are updated every week! All Pintu Academy articles are made for knowledge and educational purposes, not as financial advice.
Reference
Christy Bieber, 6 Tips to Avoid Crypto Scams, The Fool, accessed on 23 February 2023.
Coin Telegraph, What is a phishing attack in crypto, and how to prevent it? accessed on 23 February 2023.
Werner Vermaak, What Are Flash Loan Attacks? CoinMarketCap, accessed on 23 February 2023.
Jake Frankenfield, 51% Attack: Definition, Who Is At Risk, Example, and Cost, Investopedia, accessed on 24 February 2023.
Marko Mihajlovic, What Is a Dusting Attack? Crypto Exploit Explained, Shrimpy, accessed on 24 February 2023.
Krisztian Sandor. What Is Cryptojacking? How to Protect Yourself Against Crypto Mining Malware. Coindesk, accessed on 24 February 2023.
