The blockchain and crypto industry was born from the combination of various existing computer technologies. Today, crypto is an industry for various development teams who strive to create innovations to bring crypto to millions of new users. From implementing NFTs in the real world, DeFi with physical assets as collateral, to decentralized social media. Behind these innovative efforts, the foundation of blockchain technology is also constantly evolving. Zero-knowledge technology is one of the most talked-about technological innovations. It is considered to be one of the most complex technological concepts with the highest potential. Then, what is zero-knowledge and how does it work? This article will explain ZK in detail.
Article Summary
- 🔏 Zero-knowledge is a method of verifying information without revealing its content.
- 🤝 A ZK system consists of two parties: a prover and a verifier. The prover carries sensitive information and must convince the verifier without revealing the content of the information. If successful, the system will generate a zero-knowledge proof as validity proof.
- ⚙️ The verifier needs to test the prover’s truthfulness. The verifier will ask the prover to perform a series of actions that can only be done if the prover knows the right information. This is like a question-and-answer session that relies on algorithms to test using the relevant data without exposing the prover’s information.
- ⚖️ The most popular ZKP generation methods are zk-SNARK and zk-STARK. Both fall into the category of non-interactive ZKPs as prover and verifier interaction is minimal.
- 🧠 The SNARK method is more popular than STARK and has been around for a while. SNARK is ideal for systems with simple computation and low cost while STARK is the most recent method ideal for processing large amounts of complex data.
- 👩💻 The most popular implementations of ZK technology today are ZK-rollup layer 2 on Ethereum and zkEVM. Several teams developing ZK systems on Ethereum are Polygon, Scroll, zkSync, and ConsenSys.
What is Zero Knowledge?
Various technological innovations in the blockchain world are looking for ways to break through the limitations of the blockchain trilemma. A blockchain trilemma is a situation where the development team of a crypto project has to choose two out of three aspects and sacrifice one of them in creating a blockchain. One such technology is the implementation of zero-knowledge (ZK) and zero-knowledge proof (ZKP).
Read about the Blockchain Trilemma at Pintu Academy.
ZK technology itself is not new. Research on ZK technology was first published in 1985 by Shafi Goldwasser, Silvio Micali, and Charles Rackoff of MIT. The three researchers posed a simple question like this: “How can I prove that I know about a secret, without telling the secret?” This is why it is called “zero knowledge” because the party receiving and verifying the information (verifier) does not have any knowledge from the other party (the prover).
So, zero-knowledge is a method of passing information without revealing its content. The solution of the three researchers was to create proof that shows the validity of the prover that the verifier must accept as true. This proof is a zero-knowledge proof or ZKP.
Since 2022, conversations about the implementation of ZK technology in crypto have grown in popularity. Various projects announced the development of their respective ZK systems such as Polygon, ConsenSys, Scroll, and Matter Labs. Below we will explore the cogs that drive a ZK system in the context of crypto networks.
How Does Zero-Knowledge Work?
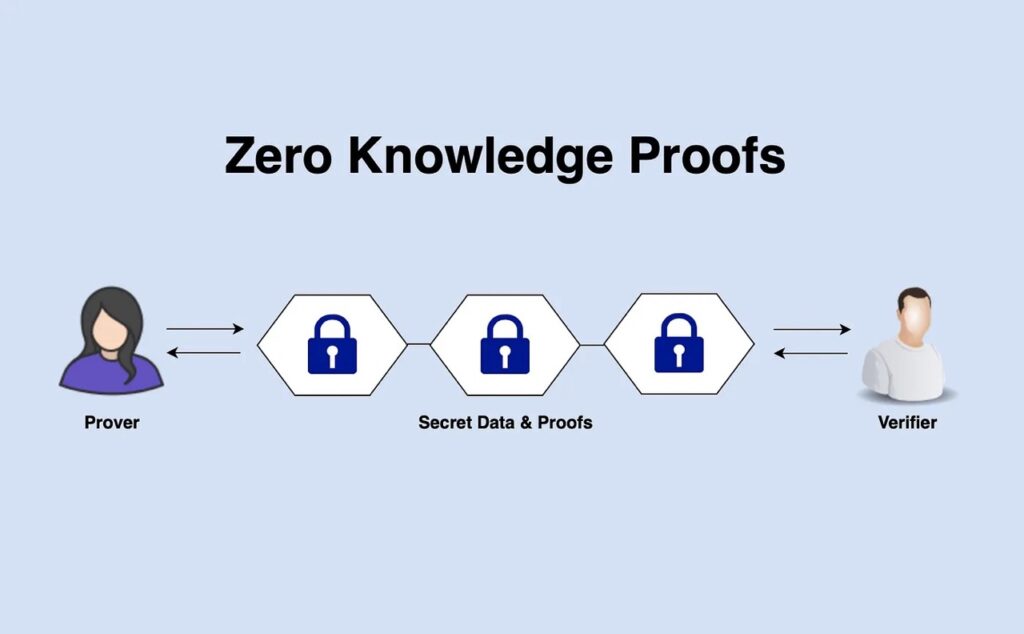
A zero-knowledge system consists of two interacting parties: the prover and the verifier. The prover is the one who carries the information and the verifier is in charge of validating the prover’s claim of truth. The goal of this interaction is for the prover to prove to the verifier that the information it is carrying is true without revealing the content of the information.
The prover and verifier system is something we're used to. When we want to log into our social media, we become the prover by entering our account password. The site we go to is the verifier that validates the password with the data on the server. As we know, there are many loopholes in this system including fraud, data mining, and hacking.
Despite its apparent simplicity, the ZK system is computationally intensive and powerful because it involves solving cryptographic puzzles that only the ZK system can read. In the context of blockchain, ZK technology has great potential because it means that user data remains secret and transactions can still be processed.
So, how can a verifier trust a prover’s data without seeing the information? The answer is ZKP. A zero-knowledge proof is a proof of validity for information. The system will generate ZKP after both the prover and the verifier agrees about the truthfulness of the information. Creating a ZKP is complex and various blockchain development teams are looking for ways to make ZKP faster, safer, and more efficient.
Zero-Knowledge Proof
To generate ZKP, the verifier needs to test the correctness of the prover’s information. The verifier will ask the prover to perform a series of actions that can only be performed if the prover knows the right information. So, this is like a question-and-answer session that relies on an algorithm to test the relevant data (which acts as a clue) without exposing the prover’s secret data.
Here is the simple process of generating a ZKP:
- At first, the verifier will ask the prover some questions.
- The prover then processes these questions and responds to the verifier.
- The verifier considers the prover’s answers and produces a ‘true’ or ‘false’ output.
- This process happens repeatedly until the prover successfully convinces the verifier, and the system issues a ZKP to validate the information.
The above method of generating ZKP belongs to interactive ZKP where the prover and verifier interact several times until the prover passes the test. However, most ZK projects now use non-interactive ZKP because it is faster. We will discuss non-interactive ZKP in the next section.
The generation stage of ZKP is similar to a game of charades, where one person knows the correct word and the other person has to guess it. Here, the person who knows the correct word can give clues about all aspects of the word but cannot tell the correct word.
So, why is zero-knowledge proof so important? Many projects are pursuing ZK systems because of the high level of privacy it provides. ZKP allows sensitive information about a person or a transaction to remain secret. It also increases security because a ZKP is very difficult to duplicate.
The process of generating ZKP usually happens off-chain so that it does not burden the main network. A ZK protocol will typically batch transactions, process them off-chain, and generate a ZKP that will be returned to the main network. So, this is how various ZK layer 2 projects on Ethereum work.
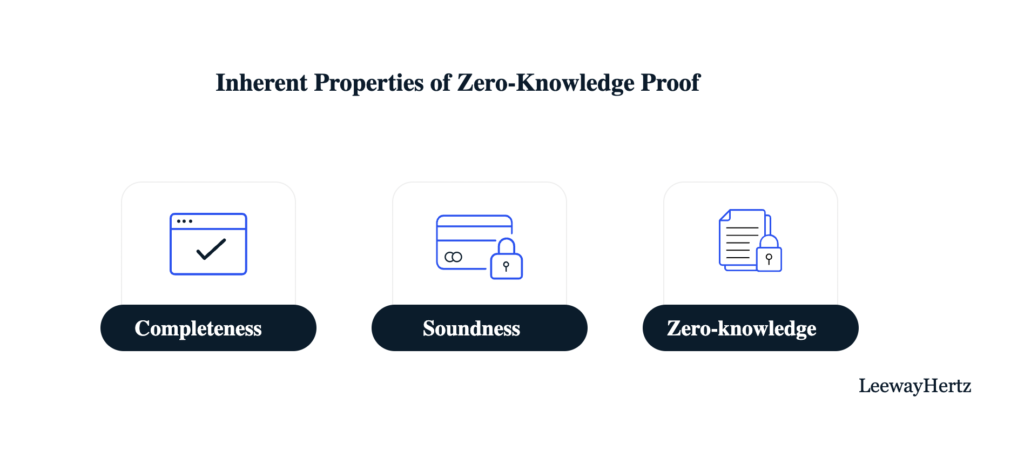
Three fundamental characteristics of a ZKP:
- Completeness: If the prover passes and meets the criteria, then the verifier will be confident in the ZKP produced by an honest prover.
- Soundness: If the prover cannot produce the right answer and does not pass, he cannot convince the verifier through a ZKP. A dishonest prover cannot fool the verifier (except due to system defects).
- Zero Knowledge: The verifier gets no additional information other than the fact that the prover carries the correct information.
Understanding zk-SNARK and zk-STARK
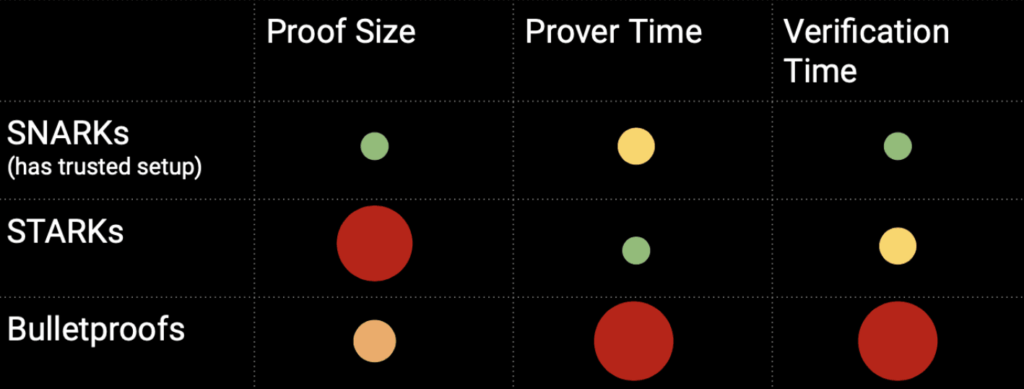
The two most popular methods of generating ZKP are Zero-Knowledge Succinct Non-Interactive Argument of Knowledge (zk-SNARK or SNARK) and Zero-Knowledge Scalable Transparent Argument of Knowledge (zk-STARK or STARK). Both are non-interactive ZKPs that use shared keys through agreed public parameters to generate ZKPs. In these systems, the interaction between the prover and verifier only occurs once.
SNARK uses a public parameter that is used by both parties to generate and validate the ZKP. This public parameter is Common Reference String (CRS). SNARK also utilizes elliptic curves to protect sensitive information in the generated ZKP. However, the drawback of SNARK is that someone must operate the CRS (called trusted setup) which means a criminal prover can see the sensitive data and create a fake ZKP.
To overcome this weakness, SNARK uses a multi-party computation (MPC) setup ceremony in the process of creating CRSs. In MPC, multiple provers provide partial information in creating a CRS without communicating with each other. Once the CRS is created, as long as one prover acts honestly and removes its sensitive data, the system operates normally. The SNARK system is very different from its more recent competitor, zk-STARK.
Several crypto projects that already utilize zk-SNARK technology include Loopring, zkSync 1.0 and 2.0, Zcash, and Mina Protocol.
STARK is an innovation created by STARKnet to create an alternative non-interactive ZKP method. STARK does not utilize trusted setups and CRS (this is why there is the word transparent in STARK) to generate ZKP. Instead, STARK uses publicly verifiable randomness to create public parameters for generating ZKP.
STARK is more scalable than SNARK because the time required to validate data increases quasi-linearly to the complexity of the calculation (the time in SNARK increases linearly with complexity). Thus, STARK is ideal for generating ZKP when transaction volumes are high or processing large data sizes. In addition, STARK uses Collision Resistant Hashes so it is resistant to attacks by quantum computers or quantum-resistant. This makes the STARK ZKP more secure and future-proof.
The downside of the STARK system not utilizing CRS is that it is more computationally intensive than SNARK. The ZKP generated by STARK also has a much larger size than SNARK. As a result, the larger size means higher gas costs.
The zk-STARK project gets direct support from the Ethereum foundation since the beginning. Now, several projects already utilize STARK including Immutable X, StarkNet, and StarkEx.
STARK vs. SNARK
| Components | SNARK | STARK |
|---|---|---|
| Ethereum Gas Cost | sekitar 600k gwei (Groth16) | sekitar 2,5 juta gwei (estimasi) |
| ZKP Size (per 10.000 TX) | 200 bytes | 135 kb |
| Trusted Setup? | ✅ | ❌ |
| Quantum-Resistant | ❌ | ✅ |
The zk-SNARK and zk-STARK systems have their advantages and disadvantages. As shown in the two tables above, STARK has a larger transaction cost and ZKP size but has quantum-resistant features and does not require a trusted setup. STARK also wins in scalability over SNARK as the time taken to generate ZKP is not directly proportional to the data size. Therefore, STARK can handle large complex data better than SNARK.
On the other hand, SNARK is ideal for implementations that require low transaction costs and complexity. The much lower transaction costs and smaller ZKP size (hence not requiring large data storage) make SNARK preferable to STARK. The relatively new technology of STARK also means that the documentation is not as comprehensive as SNARK. This makes STARK’s complexity level higher, encouraging developers to prefer SNARK.
Advantages of Zero-Knowledge Technology
- A Safe Trustless Verification System: Zero-knowledge and ZKP technologies are cutting-edge trustless cryptographic innovations designed to keep users’ data safe.
- Safeguarding Sensitive Data: ZKP ensures sensitive data is preserved because the network does not need to disclose the data when validating transactions.
- Lower Gas Costs: Transactions utilizing ZKP technology require significantly fewer gas fees as the blockchain only needs to validate a single ZKP proof.
- Faster Transaction Validation: Zero-knowledge proof technology cuts down the time required to process transactions because the network does not need to validate transactions one by one.
Several Implementations of ZK Technology
ZK-Rollup as Ethereum Layer 2

One of the most popular implementations of ZK technology is a ZK-rollup as Ethereum layer 2. So, ZK-rollup “rolls up” several transactions, processes them off-chain, and provides ZKP proofs as a sign of transaction validity (called validity proof on Ethereum) to the Ethereum main network. This method is similar to an optimistic rollup. However, ZK-rollup is more effective than OR because it only requires ZKP as proof of transaction validity.
The architecture of a ZK-rollup consists of two things:
- On-Chain Smart Contracts: The state of the ZK-rollup network is maintained by several smart contracts on Ethereum. These include the main contract that monitors the status of the network including blocks produced. In addition, the verifier contract in charge of validating the prover is also stored here.
- Off-Chain Virtual Machine (VM): The ZK-rollup transaction execution is stored in an off-chain virtual machine or VM. This VM receives and collects transactions and reports them to the Ethereum main network. Transactions are final after ZKP is sent to on-chain smart contracts.
ZK-rollup is one of Ethereum’s ideal scalability solutions. It still relies on Ethereum’s security because every transaction still needs approval by Ethereum (via ZKP confirmation). In addition, ZK-rollup’s transaction fees are very low when compared to some other layer 2.
zk-SNARK and zk-STARK also have their bottlenecks in the context of a ZK-rollup. SNARK technology is not designed to process complex transactions such as smart contracts. STARK, on the other hand, is built to handle large volumes, so small transactions will incur expensive gas fees.
However, one of the current limitations of ZK-rollup is that it is not compatible with the Ethereum virtual machine (EVM). Dapps on Ethereum cannot migrate because ZK-rollup does not use Solidity (Ethereum’s programming language). So, most ZK-rollups today do not have smart contract capabilities. Development teams need to learn a new programming language to build on top of ZK-rollup.
One of the drawbacks of ZK technology as Ethereum layer 2 is the risk of censorship and centralization. In ZK-rollup, there needs to be a validator called a sequencer in charge of collecting and sequencing transactions on the ZK-rollup chain. The sequencer has a very important role because it can censor transactions and rearrange incoming transactions. This is the weakness of all rollup systems.
So, this leads to our next topic which provides a solution to the ZK-rollup problem, zkEVM.
zkEVM
zkEVM is a virtual machine compatible with EVM and can support zero-knowledge proof computation. Furthermore, this solution was created to overcome the ZK-rollup bottleneck which can be divided into two:
- Programming language limitations: All smart contract logic in ZK-rollup uses a specialized language (such as R1CS). It not only has complicated language syntax but also demands strong expertise in ZKP.
- ZK-Rollup does not support composability: Different ZK-Rollup applications cannot interact with each other within Layer 2. This breaks the functionality of various interconnected DeFi applications.
So, zkEVM wants to make ZK-rollup like a typical Ethereum roll-up where applications are created using the Solidity language. This is to enable DApps development team to easily migrate to the ZK-rollup network. In addition, the work of developers who want to build on top of zkEVM becomes easier. zkEVM is becoming a key mission for various development teams as this could open up ZK technology to the smart contract ecosystem that exists on Ethereum.
Several teams developing zkEVM are Polygon, Scroll, Applied ZKP, zkSync, and ConsenSys. Polygon’s version of zkEVM has just been launched and is being tested while the zkSync version of zkEVM is just entering the alpha stage.
Conclusion
Zero-knowledge technology is one of the latest innovations to address blockchain scalability and security issues. The ZK method allows transactions to be verified without having to reveal sensitive data in them. Additionally, it also cuts down on transaction verification time as the network only needs to accept a zero-knowledge proof without having to process all the transactions. Currently, Ethereum is a testing ground for the development of various ZK technologies. Many development teams consider ZK technology to be the best scalability solution. So, these teams are working on optimizing ZK for various uses in the crypto industry.
How to Buy Cryptocurrencies at Pintu
Pintu has several crypto assets related to the ZK ecosystem. Some of these are MATIC, IMX, and ZEC. You can also invest in other cryptocurrencies such as BTC, BNB, ETH, and others through Pintu safely and easily. The Pintu app is compatible with popular digital wallets like Metamask to make transactions easier. Download the Pintu cryptocurrency app on the Play Store and App Store now!
You can also learn crypto through other Pintu Academy articles that are updated weekly! All Pintu Academy articles are for educational purposes and not financial advice.
References
- Pontem Network, Zero-Knowledge 101. Zero-Knowledge Proofs | Zero Knowledge… | by Pontem Network | Mar, 2023, Medium, accessed on 27 March 2023.
- Pontem Network, Part 1: Can We Kill Moloch? ZK Basics and Virtual Machines, Zee Prime Capital, accessed on 27 March 2023.
- Zero-Knowledge 201. Learn more about zero-knowledge proofs… | by Pontem Network | Mar, 2023, Medium, accessed on 28 March 2023.
- Zero-Knowledge Proof (ZKP) — Explained, Chainlink, accessed on 28 March 2023.
- Krinza.eth, A Non-Mathematical Introduction to Zero Knowledge Proof, Mirror.xyz, accessed on 29 March 2023.
- Zero-knowledge proofs, Ethereum, accessed on 29 March 2023.
- Mattison Asher, Coogan Brennan, Zero-Knowledge Proofs: STARKs vs SNARKs, ConsenSys, accessed on 29 March 2023.
- Zero-Knowledge rollups, Ethereum, accessed on 30 march 2023.
- Ye Zhang, zkEVM, HackMD, accessed on 30 March 2023.
- What is a zkEVM?, Alchemy, accessed on 30 March 2023.
